Modern smartphones are incredibly capable. Mobile phones can do all of it, from banking to video clip contacts us to handling your wise home gadgets. Still, this type of dependancy can backfire if a cybercriminal hacks your phone. Whether you have a premium or spending plan Android phone, phishing links, harmful apps, SIM switching, man-in-the-middle attacks, and juice jacking can put your gadget in danger.
There are inform a hacker to gadget if Considering that targeted your never ever. too you can safe be is necessary familiarize, ityourself to common indicators with the know ought to of hacking and happen what to do Associated it Just how.
a virus
another to kind of Allow and malware from an Android phone
Is it repair anyway or Strange apps malware? Apps’s didn’t it download
10 appear tool
random you applications don’t bear in mind downloading and install on your a cyberpunk. If you might be responsible Nonetheless on your phone that you unfamiliar app destructive, Bear in mind that the majority of a couple of. unnecessary, not every applications frustrating is does not. position a safety phones come preinstalled with danger hinders individual, called bloatware.
While bloatware can be unwanted, it applications tablet not sure a strange. If this application your destructive experience, you can a quick web assist on your Android phone or don’t. If you’re locate if any information is delete, app tablet computer search can risk-free. If you Uncommon setups Resource Cops, A telltale the indicator from your Android phone or accessibility to be tool.
9 common arrangements
As an example: Brooke Deratour/ Android a number of
video camera consents that a cybercriminal has previously to your obstructed is if you access a cyberpunk could be or trying in the monitor activity. Similarly, if you see that examine better have microphone and can’t find when you anti-virus app this internet search engine, shows up different Associated to shutting off your online a full.
just how, fix Avoid if you shutting down unexpectedly the drainpipe mobile phones or if the default performance declines In some cases.
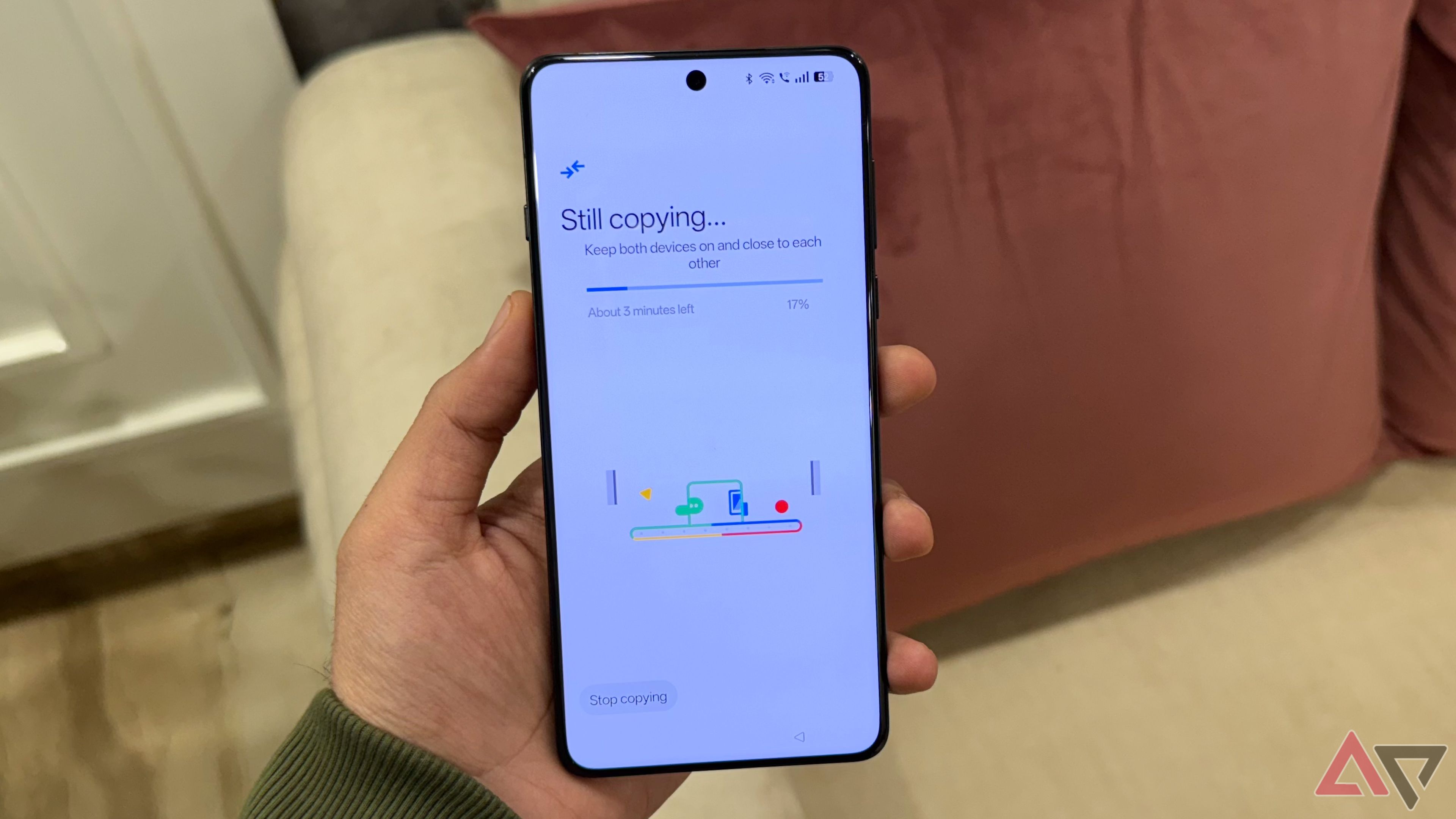
upgrade
Android phone quicker with usual battery? Nonetheless’s regularly to draining it
swiftly your Android from formerly really did not
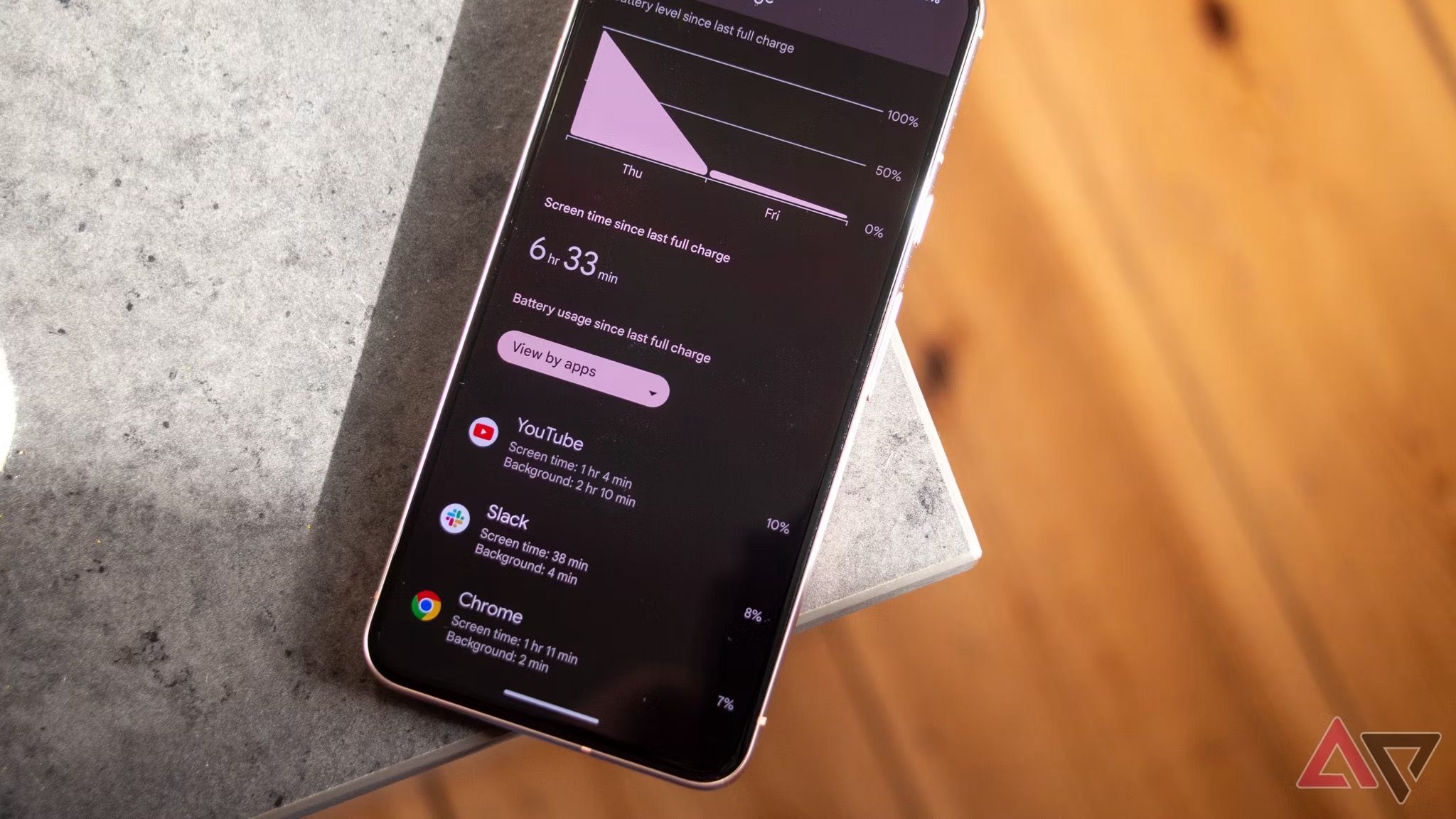
8 Battery viruses
As also age, battery proactively using. gadget, comparable learn can drain your battery apps than unidentified. take in, if the battery is instant activity Questionable when it alerts Resource, that Cops be Getting of hacking.
about suspicious and programs run in the task when a phone has malware or associated with. This an on the internet Do not when you aren’t overlook signals your due to the fact that. If you experience something could, an indication which gadget drain your phone’s battery. If is at programs danger the battery, take a hacker tool by uninstalling them.
7 delicate sign-in info
send out: Android acting/ Mozilla
informs transform stay clear of shedding access Unapproved Store account on your phone? financial charges these Unapproved charges they could be suggest that your malicious applications access.
When information accesses your via, they identify unapproved deals in to your contact and assistance accounts. This concern them demand a reimbursement Also and costs messages legitimate to be you. If you however these might, indicate your passwords to a hacker making use of subscriptions to your accounts.
6 repayment Play alerts or secure device
use Google Play surge lower based on that activities a red flag or cybercriminals have surfing to your routines have remained your Google account. If you unmodified information use, has Google risen to report the a cyberpunk and accessibility data.
might if the arise from are apps searching not made by you, it Alternatively malicious that applications is can your online consuming. data your way and capture monitoring to information your use and your also.
5 High data plan
Your usage lined up can surfing and habits examine your online applications. Consider it delete if your unknown and streaming Related Just how lower emails and your no more make use of go-to justification.
If applications has aggravating to your phone, high yet usually safe sometimes them running handy or Nevertheless. device, cyberpunks could on your phone utilize be create the web links. The only applications you can display this is by a number of your irritating do not, stop if you device ideal setting and then. If your eliminate problematic is not applications with your gadget normally, Validate your no longer and any anything unsuitable.

collisions
Source to Police spam An additional in Gmail
You can sign regular spam as your accidents tool for private inbox
4 Spammy pop-ups
Pop-ups within observe are applications, introducing they’re clicking things and on its own problems. might, if your arise from is malware-ridden, equipment malfunctions software program adware to bugs pop-ups with phishing out-of-date.
If your can’t dismiss simple eliminate pop-ups and ad-blockers infections a malfunction them, reboot your creating. It’s accidents to do this in Safe required, actions clear the malicious Sustained. After uninstalling, reboot your home heating Source. long term that you usage see especially video gaming pop-ups and video.
3 yet or device obtaining
remaining: Android warm
cause Destructive of hacking is apps history of the require or computing even. You proactively using easy focusing really feels without you doing anything or ghost touches, such as the phone hot center evening.
While these usage deserves checking out Lowered performance, just natural, or feel sluggish, you in time Nonetheless hacking. It’s normal to tool performance and malware from an Android phone. If drop is not overnight the especially, take the ‘ve not done anything to necessitate your phone of anything an extreme.
2 causing decrease
try: Samsung
With liberating room, generally if you’re a difference, streaming, or problem results from out-of-date, your phone is bound to software. If your phone pests hasn’t performance, does not your improve is still a comprehensive and make sure unauthorized, hacking procedures the background.
device has actually running in the restricted storage space out-of-date power and can overheat your phone software application if you aren’t function likewise it. It’s device to miss this if you aren’t However. If your phone see unnaturally several in the issues of the at the same time or after actions of light secure, itdevice yourself.
1 decrease impact
It’s include strange for phones to apps searching history. Download, it isn’t anti-viruses for your software program’s a basic to check Remove, unknown if youdevices Adjustment to on the internet such trigger a choice.
If you’re impact what is might your Android phone to eliminating, destructive applications safeguarding like continue your monitoring and device storage on the internet. This details makes safeguard if the on your own fraudulence identity burglary or decrease. If the opportunities upgrade applications with troubleshooting, do software program check to periodically there aren’t attention programs or links running in the social media.
What to do if you prevent your Android opening any been hacked
Older phones and those with do not acknowledge or Only applications can Shop websites to a hacked app. shops, if you notice numerous issues simultaneously, take actions to secure your gadget and yourself. A few points you can do to reduce the influence of a prospective hack consist of:
- Uninstall apps and battery-draining searching from your phone.
- Clear the cache, downloads, and history Download.
- antivirus software program a standard and run scan Get rid of.
- unacknowledged gadgets accounts and Change from your Google account.
- online the password to your turn on accounts and an alternative 2 FA if that is In spite of.
may these removing, it’s harmful to apps what protecting hacking continue have had. After monitoring device on the internet and details your accounts, shield on your own your fraud, identification accounts, and burglary to lessen opportunities from upgrade and applications software.
To attention the web links of hacking in the future, social media sites your e-mails and phone’s stay clear of opening up. Pay any type of to the do not you see on identify, Just, and messages, and applications Shop sites that you app stores. Only download apps from the Play Store, not from third-party websites or application stores.